Security
This window is used to configure security options and change the settings of WEBCON BPS Portal cookies and tokens, as well as to adapt them to the security requirements dictated by company policy.
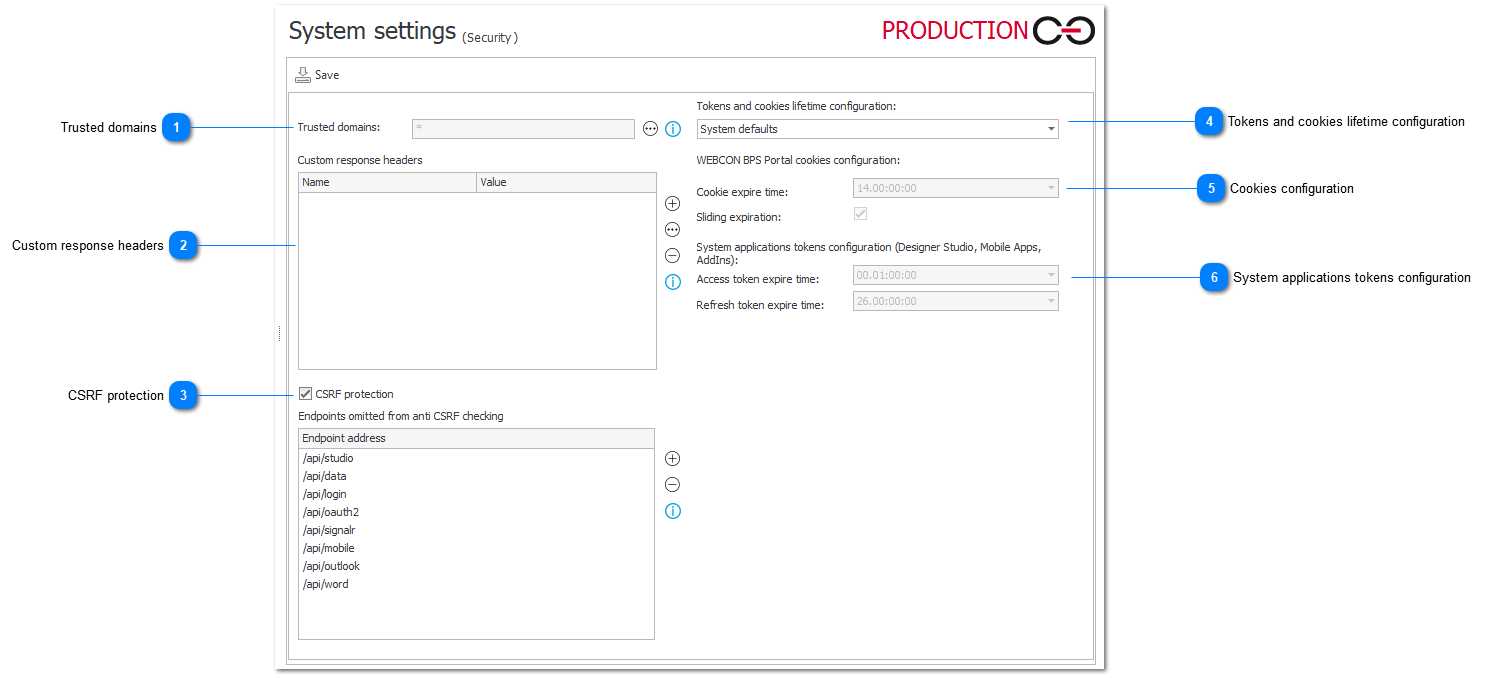
1. Trusted domains
Define a list of trusted domains on which WEBCON BPS Portal elements can be displayed. WEBCON BPS Portal elements embedded on sites in domains not included in the trusted domain list will not be shown in the browser.
This feature is not available for Internet Explorer. WEBCON BPS Portal content will always be shown in this browser, even if the site domain on which the elements are embedded is not added to the trusted domains.
In order to embed Portal in Microsoft Teams and Microsoft Outlook, add the following domains to the trusted domain list:
https://*.office365.com
https://*.office.com
https://*.microsoft.com
Note: if Content-Security-Policy headers are configured and added to the frame-ancestors section set, the list of trusted domains will be added to domains defined in this header with the exception of the “*” entry, which is ignored.
In order to ensure business continuity for existing installations, domains for MS Outlook, MS Teams and the domain of a configured WEBCON BPS Portal will be added to the trusted domains by the migration script. Removing the added entries will be possible via manual editing of the trusted domains list.
2. Custom response headers
Define a list of custom headers that will be added to every response in WEBCON BPS Portal. This allows users to match their own specific security policies.
The Content-Security-Policy header will be merged with trusted domains.
For more information, see HTTP headers in WEBCON BPS.
3. CSRF protection
Protection against CSRF (Cross Site Request Forgery, XSRF) works by checking the Origin and Referrer headers in POST invocations from the user’s browser.
A correct configuration protects all endpoints where a user is authenticated based on cookies provided by the browser.
Endpoints omitted from anti CSRF checking – checking the indicated headers is omitted for endpoints relying on token authentication. The list of exceptions should contain such endpoints.
4. Tokens and cookies lifetime configuration
Tokens and cookies lifetime can be configured by selecting one of the following options:
System defaults – predefined system values (see Cookies configuration and System applications tokens configuration)
User defined – values designated by the user
5. Cookies configuration
Cookie expire time – it is expressed as dd.hh:mm:ss. The default value is 14 days.
Sliding expiration – resets the expiration time for a valid authentication cookie if a request is made and more than half of the timeout interval has elapsed.
6. System applications tokens configuration
Access token expire time – a value expressed as dd.hh:mm:ss. The default value is 1 hour.
Refresh token expire time – a value expressed as dd.hh:mm:ss. The default value is 26 days.