Authentication providers
The node groups authentication providers and enables you to manage and control access to assets. You can go to configuration of selected authentication provider by selecting a respective provider on the selection tree.
The configuration window of an authentication provider may vary depending on the selected provider type. However, the below-described fields are always available in the configuration window:
- Active in Designer Studio – when selected, a given provider is active and available in Designer Studio,
- Active in BPS Portal – when selected, a given provider is active and available in Portal,
- Scheme – an authentication provider unique identifier (only letters and digits allowed). Excluding the providers specified in the OpenIDConnect node, the field is non-editable.
Depending on the context and specific access requirements, it is possible to use the below-mentioned providers.
Admin access
The provider enables you to log in to WEBCON BPS Designer Studio as a global administrator directly after system installation (the provider cannot be activated for BPS Portal). Consequently, you can conveniently configure system settings and complete environment configuration. However, it should be noted that the global administrator is not permitted to modify processes and applications.
The Admin access authentication data is defined during system installation. After its completion, such a provider (operating under the BpsAdmin scheme) will be the default authentication provider. It is recommended to log in with such authentication data also in emergency situations or unexpected system errors.
Windows Active Directory
Microsoft's catalogue service that enables centralized management of users, groups, and assets within a network. The AD authentication provider checks authentication data within the context of Windows environment.
Users can activate AD authentication provider in both Designer Studio by checking the Active in Designer Studio and Portal (the Active in BPS Portal button).
Azure Active Directory
The cloud identification and access service from Microsoft. It allows you to authenticate users in cloud, thus granting them access to assets located in the Microsoft Azure cloud.
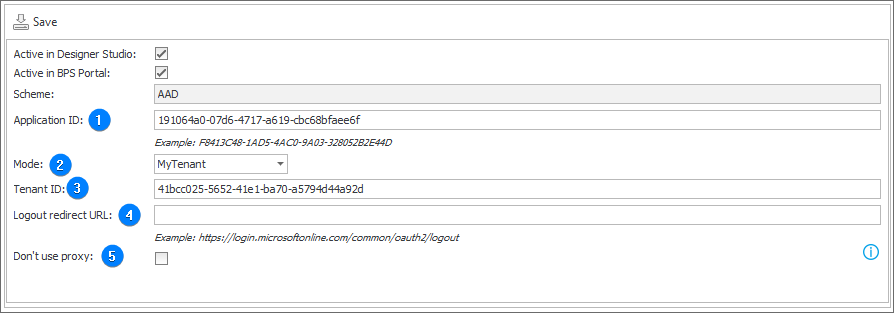
1. Application ID
Enter unique identifier of the application obtained after its registration in the Azure Active Directory service. The identifier is utilized to explicitly identify the application during the authentication process.
2. Mode
The selection list allows you to choose one of the available modes:
- MyTenant – users are authenticated only within one, specific Azure AD tenant,
- MultiTenant – the application supports several Azure AD tenants, thus users are authenticated within the context of multiple tenants.
3. Tenant ID
The tenant identifier indicates a specific Azure AD tenant where the application is registered.
Provision of a correct Tenant ID in the application configuration is particularly important, as it allows the Azure AD service to identify to which tenant environment the authentication request applies.
4. Logout redirect URL
The address to which users are redirected by the service after logging out from the application. When left empty (the field is optional), users are redirected to the Portal logout page.
5. Don't use proxy
The field determines whether the BPS Portal outgoing connections with authentication provider are to use the proxy server defined in the system. If the option is unchecked, but the system global configuration lacks defined proxy server, authentication requests will be delivered to the provider without utilizing the proxy server.
To learn more about integrating WEBCON BPS with Azure Active Directory, read the ARTICLE available on the WEBCON Community website.
ADFS
Active Directory Federation Services (ADFS) is an access and authentication service that enables single authentication (Single Sing-On) in an environment with both local Active Directory environment and external applications or cloud assets.
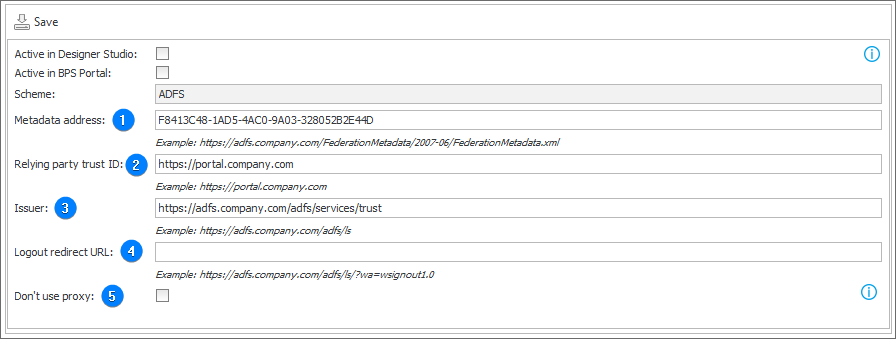
1. Metadata address
The field specifies the address of the ADFS server metadata file. You can obtain this address in the management console after logging in to the ADFS server (the AD FS folder on the selection tree → the Endpoints folder → the Metadata section).
2. Relaying party trust id
The application identifier in ADFS, i.e. the address of WEBCON BPS Portal.
3. Issuer
The issuer address, i.e. the address of an active endpoint of the WS-Federation protocol in ADFS.
4. Logout redirect URL
The address to which users are redirected by the service after logging out from the application. When left empty (the field is optional), users are redirected to the Portal logout page.
5. Don't use proxy
The field determines whether the BPS Portal outgoing connections with authentication provider are to use the proxy server defined in the system. If the option is unchecked, but the system global configuration lacks defined proxy server, authentication requests will be delivered to the provider without utilizing the proxy server.
To learn more about integrating WEBCON BPS with ADFS, read the ARTICLE available on the WEBCON Community website.
OpenID Connect
The OpenID Connect authentication provider enables WEBCON BPS users to be authenticated by external identity providers by utilizing the OpenID Connect protocol. The authentication is based on the Authorization Code Flow.
In the configuration window, enter a unique scheme name that will identify this authentication provider in WEBCON BPS. The scheme name will be visible next to the login of a logged-in user in Portal. The display name will be visible to users in the login window when choosing a provider.
For the remaining fields follow the guidelines of the external identity platform.
An external identity platform may require you to register the exact return address at which the user's ID token will be sent. The address is generated based on the authentication provider's scheme and has the following form:
https://<adres_portalu>/<signin-schemat>.
An example of an address for Auth0: https://testportal.webconapps.com/signin-auth0
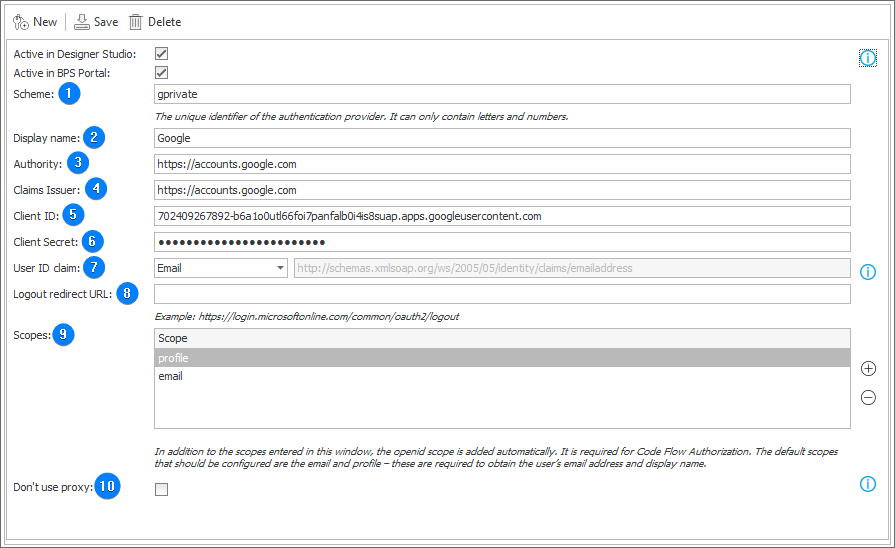
1. Scheme
The unique name of a scheme that identifies a given authentication provider in WEBCON BPS. This scheme will be visible next to the login of the currently logged-in Portal user.
2. Display name
The name that is visible for users in the login window when selecting a provider.
3. Authority
The data delivered by the authentication provider (for Google: https://accounts.google.com/).
4. Claims Issuer
The data delivered by the authentication provider (for Google: https://accounts.google.com/).
5. Client ID
The ID of the application registered on the provider's side (For Google, you can obtain the client ID by navigating to the Credentials page on the APIs and Services website).
6. Client Secret
The password for the application registered on the provider's side.
7. User ID claim
The specified claim should contain the user identifier which will be used as a BPS ID (the user's unique login/identifier) in the system. By default, this is the UPN name or an email for external users.
8. Logout redirect URL
The address to which the user is redirected by the service after logging out from the application. If left empty (the field is optional), the user is redirected to the Portal logout page upon logging out.
9. Scopes
The list of data required by the BPS platform for the purpose of identifying users includes the email and profile scopes by default. These scopes are utilized for retrieving the user's email address and display name. For other OpenID implementations, it might be necessary to add additional scopes.
10. Don't use proxy
The field determines whether the BPS Portal outgoing connections with authentication provider are to use the proxy server defined in the system. If the option is unchecked, but the system global configuration lacks defined proxy server, authentication requests will be delivered to the provider without utilizing the proxy server.
To learn more about configuring the OpenID Connection authentication provider, read the ARTICLE available on the WEBCON Community website.